TL;DR Yes. It is actually possible (technically speaking) to hack or tamper Indian EVMs but you need to have a lot of things going your way to pull off something like this. Election Commission of India has done its part to make it as difficult as possible.
Disclaimer: The following article has been written only for educational and research purposes to show the vulnerabilities in the current system. The author holds no responsibility if someone decides to use this hack in real life using the content of the article below.
Background
Well, this was not my primary choice for my second tech post. I was working on a bigger problem but I am still stuck on finding a proper implementable solution. This problem came about when I was browsing the web and found this news article which states that Election commission will hold an open hackathon for anyone who wants to try to tamper with it. I thought it was an exciting challenge because, if not for the hacking stuff, you would get to learn quite a lot. I posted about it on FB and few friends were commenting on how someone might be able to a hack an EVM.
Problem Statement
It was a fun discussion which really got me thinking. “Assume you were given the task of hacking the Indian EVMs. How would you do it?” Following article is how I attempted to take on the challenge.
First, understand the “user” requirements. Suppose somebody wants to find an exploit in the EVM (Electronic Voting Machine) and utilize it, then what would be their needs per se? Here are a few which I could think of,
- Use it to manipulate the votes actually polled (Duh? Most basic requirement, I suppose)
- Use the exploit in such a way that he/she won’t get caught doing it. (As discrete as possible)
- Desirable to have it to be a plug and play solution (Leave no evidence behind for it to be found out later)
- Should ideally circumvent all the security checks currently enforced in the system.
Now before we jump into finding an exploit, we should first understand the EVM hardware and the entire ecosystem which comes with it. Since I don’t have access to an EVM to hack in real life (Its always locked and stored away under security), I must make do with whatever information is out there in the public domain. I should study and analyze anything and everything about it, which is freely available.
Current System
The EVM
From the wiki, an EVM (as shown in the picture below) consists of 3 parts
- Control Unit
- Balloting Unit (which contains the candidate names)
- 5m long interconnecting DB9 Serial cable with one end connected permanently inside the Balloting unit.
I think the entire hardware design of the system was handled by Bharat Electronics Limited(BEL), Bangalore and Electronics Corporation of India Limited(ECIL), Hyderabad and industrial design portion was done by Profs in Industrial Design Centre(IDC) in IIT Bombay.
Let’s go through the process of voting with an EVM.
When a voter wants to register a vote, the officer handling the control unit, after verifying the credentials of the voter, presses the large Blue Ballot button which enables the Balloting unit to accept the input from the voter. When voter comes and presses on one of the many blue buttons to register a vote against a candidate, a loud beep is sounded and the vote gets stored and saved in the Control unit. Even if one presses that button further or any other button, no further vote will be recorded as the machine gets locked till control unit activates it again.
Once the whole voting process is done, the polling officer presses the black button on the Control unit and closes the poll. Now the device is powered off and the interconnecting cable disconnected. Control unit is now stored under security protection till the vote counting day. On the vote counting day, control unit is used to display the results of the poll and the winner is announced.
EVMs are powered by a 6V alkaline battery pack so that it can be used in areas where there is no or intermittent electricity.
Election Ecosystem
Since you now know about the device and the poll day, let’s focus on everything before it, like the pre-poll preparation, device checking, security measures etc. After all, for you to pull off a hack you would need to know the entire ecosystem to find a vulnerability.
I suggest going through the link here. There are around 10-12 videos(1-5min) which explain the entire process. I watched the entire thing a couple of times. I wouldn’t want to go through the entire details of the process, but here is the gist of it.
- The entire system is pretty foolproof and secure.
- Each EVM undergoes a thorough testing procedure before being used in a poll and all the testing is done by engineers in presence of the representatives of the parties and video recorded.
- Proper working EVMs are put through mock polls of 1000 votes and results are signed off and verified by all party representatives.
- Working EVMs are sealed and numbered with a pink paper seal going around the device. These are the kind of paper seals used in currency notes. ID of the seal is paired with the EVM’s device ID and stored. This makes opening the device impossible, to access the electronics guts of the device, to have any chance of tampering with it(No luck there 🙁 ).

- EVMs are randomized so that we really can’t say beforehand which EVM goes to which constituency during election time.
- Day before the polling, each EVM is tested at the polling booths with a mock poll being conducted in front of the party representatives ensure the votes are registered properly and mock poll results are correct. A Mock poll certificate is to be generated and signed off on by all party representatives.
So, all in all, it’s a pretty tight ship to break into.
Let’s see now what might be the obvious loopholes which we can consider to hack the hardware.
- Re-flashing the code written in the embedded main controller
- Physical hardware hack of the device/changing the circuitry inside
Since it can’t be done at the polling station end because of the physical seals, it needs to be done at the manufacturer’s place.
Again it’s not possible, because people have already plugged this loophole by using single flashable ICs(Meaning code can be flashed only once- Source Page 3 ) and they would most likely be doing a checksum verification. Anyway, even if we are able to reflash the device, what good will it do since you can’t be for sure the candidates position in the Balloting unit so far ahead. SO, this is also ruled out completely.
This is pretty much ruled out because of all the seals on the device. We really can’t access the electronics inside without breaking the seal.
So, what now then? Do we give up and go home? Nope. We dig deeper till we can find a suitable hack.
The Hack
Since all the above techniques were debunked, let’s examine the weak link of the entire chain to get an entry point.
- Time of attack
As explained above, there are tests, checks, rechecks at each point till the poll day. So, our hack can only materialize on the polling day (Maybe in morning) or once the EVM has reached the destination polling booth and setting of the candidates name and orders has been done.(Maybe just before or after the final mock poll)
After thinking about it for quite some time, the weakest link for me is the third part of the EVM, which is the Serial Cable. The good old Serial cable. The vital part of the system which carries ALL the important data between the Balloting unit and the Control Unit like the votes being cast.
Now we go back to our “user” requirements and see how to formulate a hack on this weak link. The data after being stored in the control unit can’t be messed around with since we can’t access it (The bloody paper seals…) We need to modify the incoming data to the Control Unit. Now again, we can’t access the internals of the Balloting unit so how do we modify the data then?
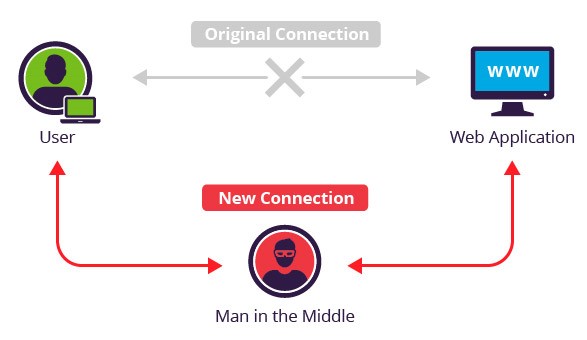
It needs to be modified on the Serial cable. In computer security terminology, doing something like this is called Man-in-the-Middle Attack(Wiki). A basic example is if, A and B are communicating with each other, and there is an attacker C which comes in between A and B, listening to the communication and possibly altering the communication between two parties who believe they are directly communicating with each other.
For a web based system it looks like the following. Image Courtesy: Incapsula
Now our job is to design a Man-in-the-Middle Attack as discretely as possible. We really don’t need much to pull off such an attack. A Serial Sniffer (A device in series after the cable and before it goes to the Control unit) in the serial cable would solve the problem. But our challenge is to design one so small that it goes practically un-noticeable in the whole system.
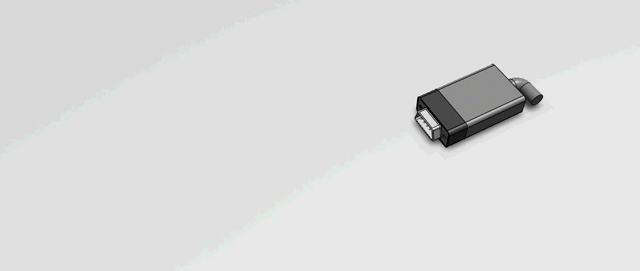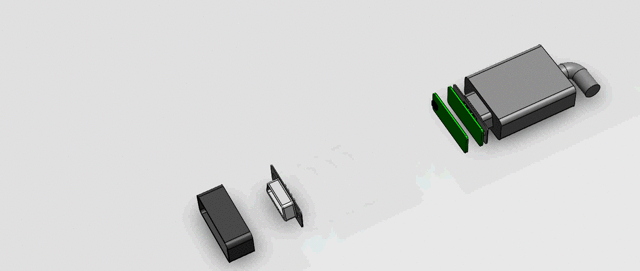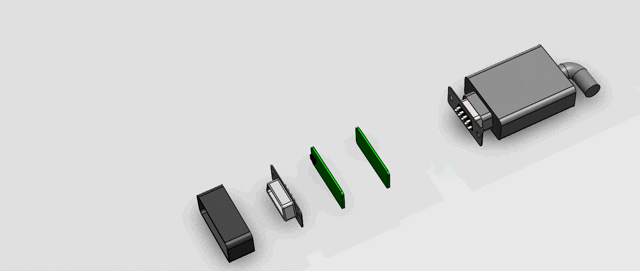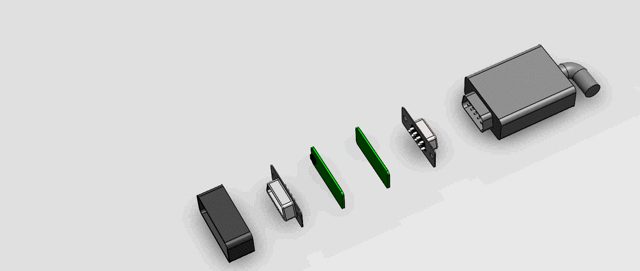
If we observe the serial cable carefully, you will notice that it consists of a DB9 connector, one end of which is permanently connected to the Balloting unit and the other end goes to the back of the Control unit.

Serial Cable connects to the Ballot Unit Connector on the left side.
Now here we must make some real-life assumptions. Since I don’t have access to an EVM to test or verify let’s take some educated guesses.
- Since they are using DB9 connectors, I am assuming they are using UART protocol which I believe is a safe assumption to make because engineers designing the system adhere to(atleast most of the time ?) proper standards.
- Voltage levels in the Serial line is a hard one to figure out, but it can be either R232/R485 levels ( -15V to +15V levels) or TTL levels (0-5V or 0-3.3V). Based on the few pics of the EVM lookalike pictures of the PCBs which I have seen online, I haven’t seen a RS232 converter so I believe it’s safe to assume the signaling is 0-5V — This assumption actually doesn’t matter much because we can modify the Sniffer circuitry to handle the signal voltages, if needed.
- Encryption of data being transmitted over the cable.
This for me is one of the guesses we must make which is slightly in the unclear area. I am inclined to think that earlier versions of the EVM might not have contained any encryption but the 2009 newer model might have some sort of simple encryption/coding done on the software level. Again, based on the pics I am seeing online, I am not seeing a dedicated encryption circuitry.
So here I go with assumption that they are either totally unencrypted or that some may contain some sort of simple encryption or coding which can be cracked with let’s say, couple of days of debugging the Serial data of an EVM with a logic analyzer. If that’s the case, decryption algorithm can be built into the Sniffer’s logic.
Let’s be honest here, I am sure I am not the first person to think of a Man-in-the-Middle attack on the serial cable. I am sure, team designing the system from ECIL and BEL might have thought about it. I am assuming that, they might have thought the Sniffer device would be a device which noticeable, which would probably be been seen by someone handling the system since the serial cable is actually exposed to general vies and anyone walking into the polling booth. If that’s the case, I am sure we can design something so small that its actually not noticeable unless you are looking for it. That’s just a design problem.
Electrical Design
So, what do we want our device to do? It should be able to read the incoming UART signals from the balloting unit, do some processing on it (modifying it) and send the modified signal to the Control unit.
Obviously, we need a small microcontroller to handle and modify the data stream. Since we can’t have a battery, a power supply regulator is needed take in whatever is the input voltage from the DTR line of the UART and convert it to the required voltage requirements of the microcontroller. Emphasis now is to make the circuitry and device extremely small.
On searching around for the smallest controller, I came across a 6pin controller from Atmel (Now Microchip) Attiny10 which has 4 I/O ports we need (2 for data in and 2 for data out) and fits the size of 2 x 2 x 0.5mm (l x b x h) which is perfect for our needs. Only problem with that one is it has only 1KB of program memory so assuming if we need to do some good amount of processing (i.e. if line is encrypted) we might not be able to do it in 1KB program space.
So, I am thinking of going ahead with something a bit more powerful and something which has Bluetooth capabilities. IC CSR8510 would bit the bill with a package size of 2.57 x 3.21 x 0.6mm. We might need Bluetooth capabilities if let’s say, we want to modify the data on the fly(But it increases the risk of getting caught also as it can broadcast the Bluetooth device name in the public)
As I mentioned earlier if the protocol used is RS232 then we would have to have a driver IC for voltage translation. MAX232 would fit the bill with two input and two output drivers. Size: 5 x 4 x 1mm (Again not so large).
We can go ahead with picking a low dropout voltage regulator which is small, from the LM1117 series, depending on the voltage requirements of the controller we use. Apart from these, there isn’t much in the circuit except for the passive capacitors/resistors. So, real estate needed for the circuitry isn’t that much.
I am not providing a schematic here for the simple reason that circuitry is simple enough to be built by anyone with decent knowledge in electronics with the components mentioned above. (Also, I didn’t have the time to draw one. ? )
Mechanical Design
Here the constraint now is to design something that is un-noticeable as possible. One end of our serial cable is open and it connects to the back of Control unit by opening of flap on the back of the control unit. This section is not usually seen outside as it resides inside the flap(Check this video). So that’s where we want our sniffer to be.
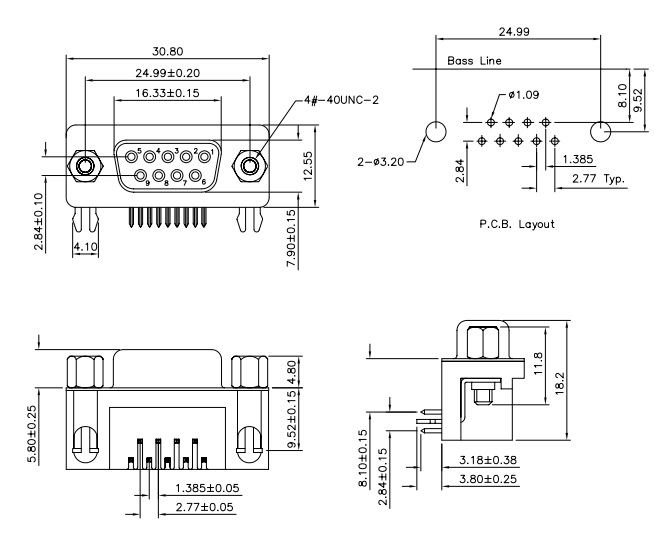
The sniffer attaches itself to the cable and the modified cable is plugged in to the Control unit. The dimensions of a DB9 connector which connects to PCB with a 90° bend is as follows
As you can see, the horizontal width of the cable head is 30.8mm and the connector takes up 16.33mm in space already. The Serial connector is terminated with a male header and Control Unit with a female header, hence our sniffer should have a female header and a male header on both its ends. Now a question arises as to where do we fit all the electronic components? Remember in the earlier section, we were noting down the dimensions of the ICs? That was exactly to fit it all in a small space.
After a few trials, I decided to go with a 2 PCB arrangement for PCBs (Each being 1mm thick) attached back to back and interconnected with each other with exposed pads. The rear end of both the male and female DB9 connectors gets soldered on to each separate PCB. Since we can’t put any components below those pads, we have to fit our microcontroller, regulators and passives on both sides of the connector. i.e. in a space of (30.88mm-16.33mm)/2 =7.3mm. We will fit the ICs in this rectangular section of 7.3mm x 12.55mm. When we did a rough mock up, ICs fit snuggly.
Now we need a casing to encase the entire thing. If you check out the Election commission videos, you will notice that the end of the Serial cable is black rectangular block which houses the male DB9 connector. For our hack to be foolproof, we need our casing to match the dimensions and color, which is relatively an easy task to do in the plastic manufacturing industry.
Here is what our Serial sniffer will finally look like.
Thanks to my buddy Avinash Iyer for 3D modeling this mockup in under an hour. Kudos to him. ?
The Sniffer section is colored differently in the rendering to make it look distinct. Ideally it will follow the same design of the existing cable to make it appear absolutely seamless. (Apologies for not making the cable look exactly like in the video, we were a bit short on time ?) The two green PCBs house the electronic parts and connects the 2 ends of the male and female headers.
The entire Sniffer device would be around 12mm long (same as the metal connector head of a normal USB pendrive) and with some optimization in mechanical design I am sure we can bring it under 10mm, which for me would really make it fall in the unnoticeable category. (Yes, I do agree you will be able to notice it if you are looking for it)
Execution
Now that we have got the device. How do we execute the hack? As I mentioned before, the best time for this would be sometime after the mock polls are conducted. For this hack, you would definitely need to have poll officers under your influence as he/she will be in charge of setting up the final device. A 12mm long device will fit in any pocket/purse so that you can sneak it in without raising any alarms.
On the day of the polls, while the instrument is being setup, one can easily slide this sniffer on the end of the Serial cable in a couple seconds before plugging it into the back of the control unit. Since there is a flap hiding it from normal view, it’s very hard to notice its even there.
Once its installed there, let’s assume we went ahead with the Bluetooth version, we can easily do a device firmware update via an Android app to select which candidate number to prefer in that polling booth. If we go for the non-Bluetooth version of the controller then we need the sniffer to be reprogrammed with a candidate number based on who should be favored. This is fairly simple as the list and order of the candidates on the ballot unit are usually known at least a week in advance.
The program in the controller can be configured to be activated only after let’s say 150 votes(So that it might pass a random mock test conducted) or it can be triggered to activate when a particular sequence of votes are casted.(Bunch of friends staying together in the voting line and voting in a particular sequence like ABBAC). To avoid suspicion of the votes being cast, we can actually formulate an algorithm which steals votes from the other candidates for every 3 votes casted and changes it to the candidate of user’s choice.
Once the polls are done for the day, while dissembling the cable, the poll officer can easily plug out the sniffer without anyone noticing. Thus, you have hacked a polling booth to your advantage.
Yes. I know scalability is an issue here, meaning you would need have one person under your control in every polling booth available. But, in reality, it would not be much of an issue as you are not looking to hack to every poll booth out there, you are only trying to sway the votes in critical poll stations so as to not arouse much suspicion.
How can Election Commission prevent this?
Now that we have wrapped up the hack, and we know for a fact that such a vulnerability exists, how can we work to prevent such an act? Let’s think about this from the other side.
- If the vulnerability is in the open communication line that’s what we need fix upfront. We can use an extremely secure 128bit AES encryption with the help of additional hardware encryption ICs. This might be an overkill for our needs but hey ?. It would take even the fastest super computer a 1 Billion Billion(1018) years to brute force crack a 128bit AES encryption.
- What makes our hack work is that we are not sealing off the back panel from access or currently there isn’t any protocol for checking that. If we make mandatory check of the cables and connector in front of the party representatives before the poll begins and they all sign off on it. It will render the above hack to be obsolete.
Conclusion
We can safely say with a fair amount of certainty that the above hack is a possible scenario and we need to plug it in some fashion. But you need to hand it to the Election Commission of India, ECIL and BEL for making it extremely difficult to find an exploit in the system and to have rectified the potential problems with stricter security protocols in the conduct of the election based on feedback.
One good thing about the current system is that they have made it un-connectable to the internet which would have made life easier during poll counting but would have opened a new can of worms for hacking scenarios.
There was a detailed paper written about hacking of the EVMs by Alex Halderman and Hari K Prasad back in 2010. You can read about it here. Here they replace the display on the Control unit and then do a manipulation on the device. This is the paper which everyone refers to while criticizing the EVMs. Although I do think paper does a thorough analysis of the topic, but manipulating the hardware by opening it up, is a security flaw which Election commission has fixed with tamper proof paper seals.
To conclude, although the above hack is technically feasible, to implement it in real life you really need to have a lot of things (like money, influence etc.) going your way.
I am currently going through few long official documents from the Election Commission regarding EVMs so I might update this article in some time if I find any new information worth sharing.
This was a fun exercise for me ?. Really enjoyed the challenge to find a loop hole in the system. Hope it was worth your time.
Do let me know in comments or via email at amaldev.000@gmail.com if there are any issues with the proposed hack or if there any other ways which I didn’t think of.
If you enjoyed this one you might enjoy my following post as well on
How to Track your ₹2000 Currency Notes
OR
you can sign up for the spam free newsletter which will allow you to get update mails whenever I write a new tech article. ?
Happy Hacking…
Post Script
Update: May 2nd 2017
Its been two weeks since I published this post and I have been getting few feedbacks/connect requests/phone calls just on this blog post. I have also been taking with a couple of experts on this topic and reading up on few more documents from the Election commission. I thought I should update this post with some new info below.
There was a Election commission Expert committee report on technical evaluation of upgraded EVMs(Download Here, Source). This report mentions the remote possibility of such an Man-in-the-Middle attack on the serial cable and has recommended to introduce dynamic coding of Key numbers to enhance the security of the data transmitted between the ballot unit and the control unit. What this means is, each of key strokes while voting, would have been encoded with probably a session key which changes at every vote-count in the newer models of EVMs(older units prior to 2009 would still be un-encoded). I am not sure what sort of encoding they use, but unless its a strong encryption(Which I doubt looking at the ICs on the device, based on pics online), a potential hacker would be able to sniff the line enough number of times before hand and decode the signals(and the key) with enough amount of recorded encoded signals. Hence my recommendation of 128bit AES encryption for future models is still valid .
I have talked with an expert on the EVMs and he(or she) has mentioned that the newer model of EVMs(I think its model 3 or model 4) which are being designed right now(potentially for 2019 elections, but I dont know how many can made and deployed by then) have an even greater level of encryption on its communication line, which would eventually disable this hack. Good to know 😀
Another information I would like to add is the introduction of Voter Verified Paper Audit Trail or VVPATs(Read in detail here). They are devices which will sit in between Ballot unit and the control unit and would print and display the votes in real time to the voter. When the voter presses on the candidate he wants to vote, the VVPAT machine will print(on thermal paper) the details of the vote, will display it to the voter discreetly for 5-6sec and then drop that paper in a box automatically. Thus physically registering a vote on paper as same as the one voted by the voter. So in-case there is a discrepancy, the printed votes can be counted. Its a good initiative but I am personally of the opinion that we are using another electronic device to secure an electronic device, so effectively opening up opportunities for new exploits. If the original device can be made as foolproof as possible, such a device might not be needed. But I think VVPATs will be a short term solution to instill security in the minds of the public.
A Connection schematic for the VVPAT would be as follows
Ballot unit —> Serial cable 1 —> VVPAT —> Serial Cable 2 –> Control unit.
If they are looking at VVPATs as a long term solution to the problem, they might as well design Ballot unit and the VVPATs in a single module like one of those credit card swipe machines at retail stores(with receipt printing and) with a storage compartment connected to the control unit.
If anyone is interested they should also read through this letter(Page 9 ownwards) from Election Commission answering few questions asked by a citizen regarding the EVMs.
I want to conclude by saying that EC has been active in taking steps to secure the system whenever somebody has made a valid suggestion to them. Kudos to them for that. I do hope they continue to do so in the future and plug any holes(if any) because fair elections are the basis of a good democracy.
Once again, hope you enjoyed the post. Thanks again for all the feedbacks and rebuttals.