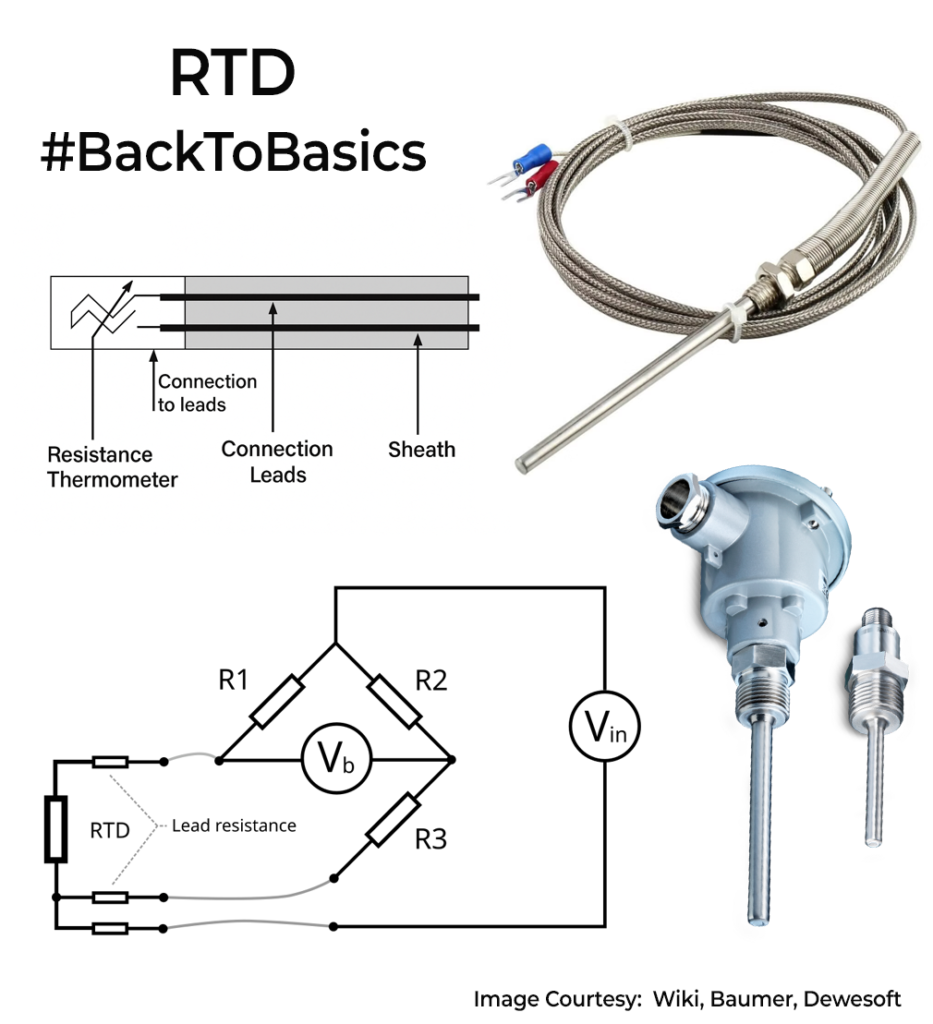
I was exploring tech for some non-destructive testing and came across Neutron Imaging. Felt it was interesting enough to discuss on a post.
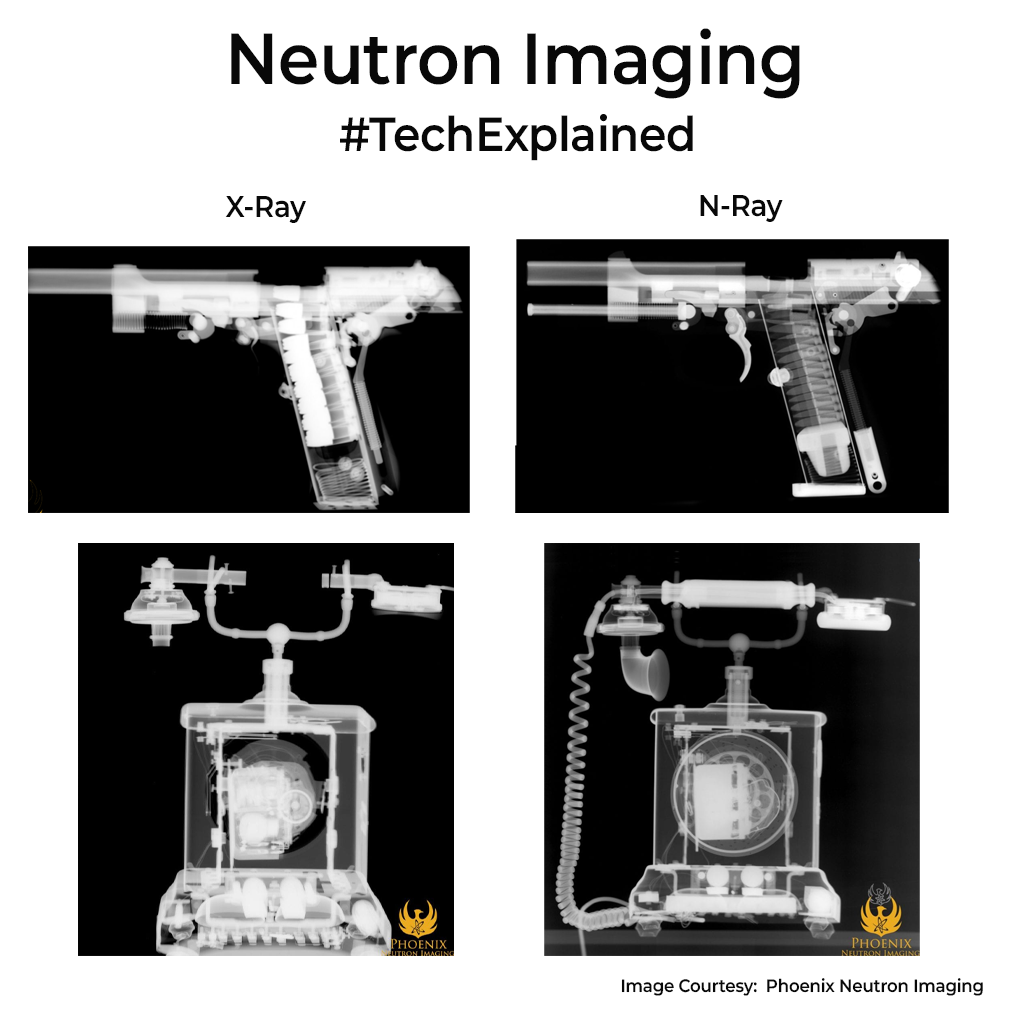
Neutron imaging uses neutrons to probe inside objects by interacting with atomic nuclei, so it reveals light elements (hydrogen, lithium, boron) hidden in heavy metals. The tech dates back to the 1940s, when early work produced the first radiographs of mechanical parts.
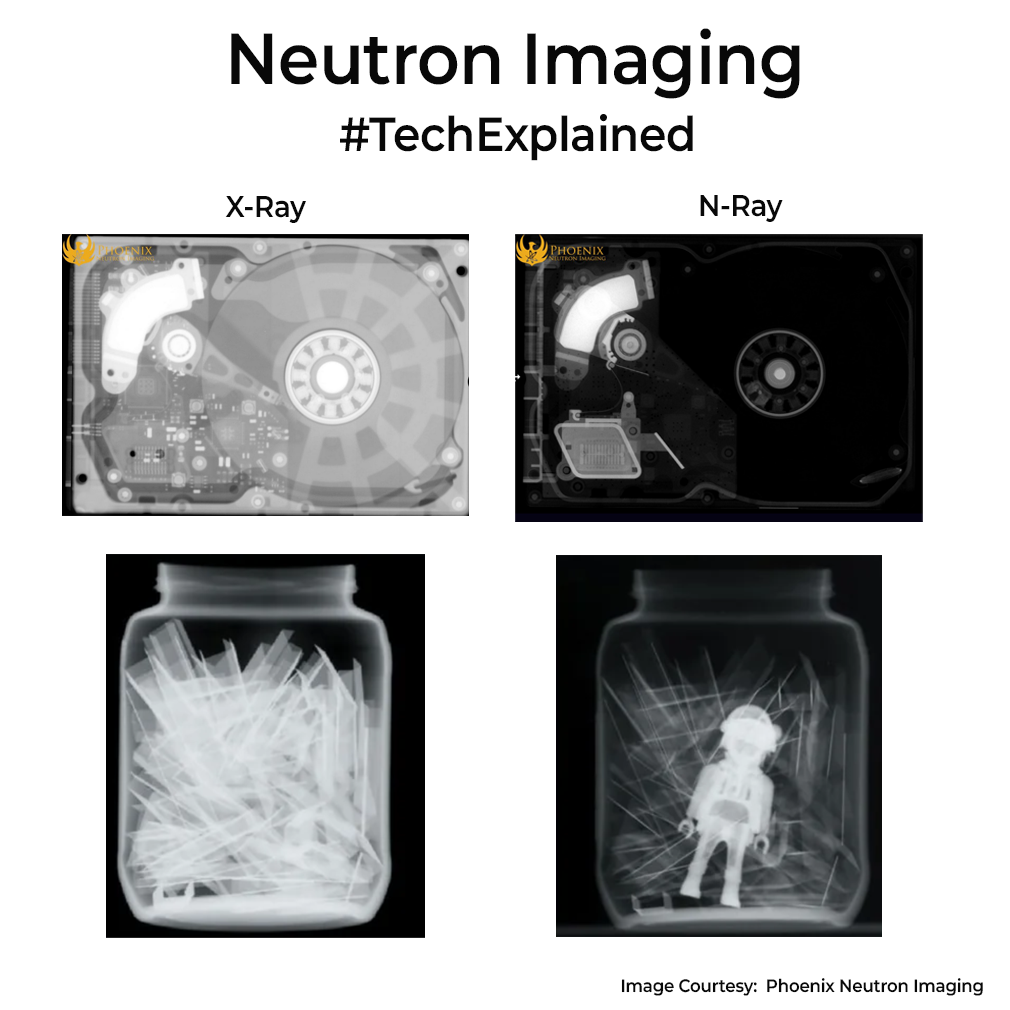
In a typical setup, reactors or accelerators generate neutrons, moderators slow them, and collimators shape a focused beam. As neutrons pass through a sample, materials attenuate them differently. A scintillator converts transmitted neutrons into light, which is recorded by a camera for 2D images.
The science behind it is all about contrast mechanisms and energy dependence. Materials rich in hydrogen show up dark, while dense metals can be almost transparent. Thermal and cold neutrons (at energies around 0.025 eV or lower) give high spatial resolution, whereas fast neutrons (in the MeV range) penetrate thicker samples but sacrifice some contrast. By rotating the object and collecting many 2D images, you can reconstruct a 3D map of internal features, much like a CT scan.
Compared to X-rays, which excel at imaging heavy elements and bone due to interactions with electrons, neutron imaging complements them by highlighting light, often organic, materials inside metal casings. So both these techs are complimentary. Check the images for differences.
It has applications in visualization of internal components in automotive and aerospace industries to detect defects, and assesses hydrogen distribution in fuel cells as well as lithium concentration, Li-metal anode structures, and electrolyte dispersion in Li-ion batteries. I do think they have a use case in airport baggage screening machines to see what X-ray/CT machines fail to capture. But might be too bulky/expensive for routine checks.
PS: Neutron imaging can even map water intake inside a plant root, something X-rays simply can’t capture.