This week lets discuss RTDs or Resistance Temperature Detectors.
They’re simple sensors where the resistance of a metal element changes predictably with temperature. So how does it work? As the temperature rises, the vibrations in the metal lattice increase, scattering electrons and raising resistance, which can be measured. They are not thermocouples. A thermocouple uses two dissimilar metals, while an RTD uses a resistive wire element.
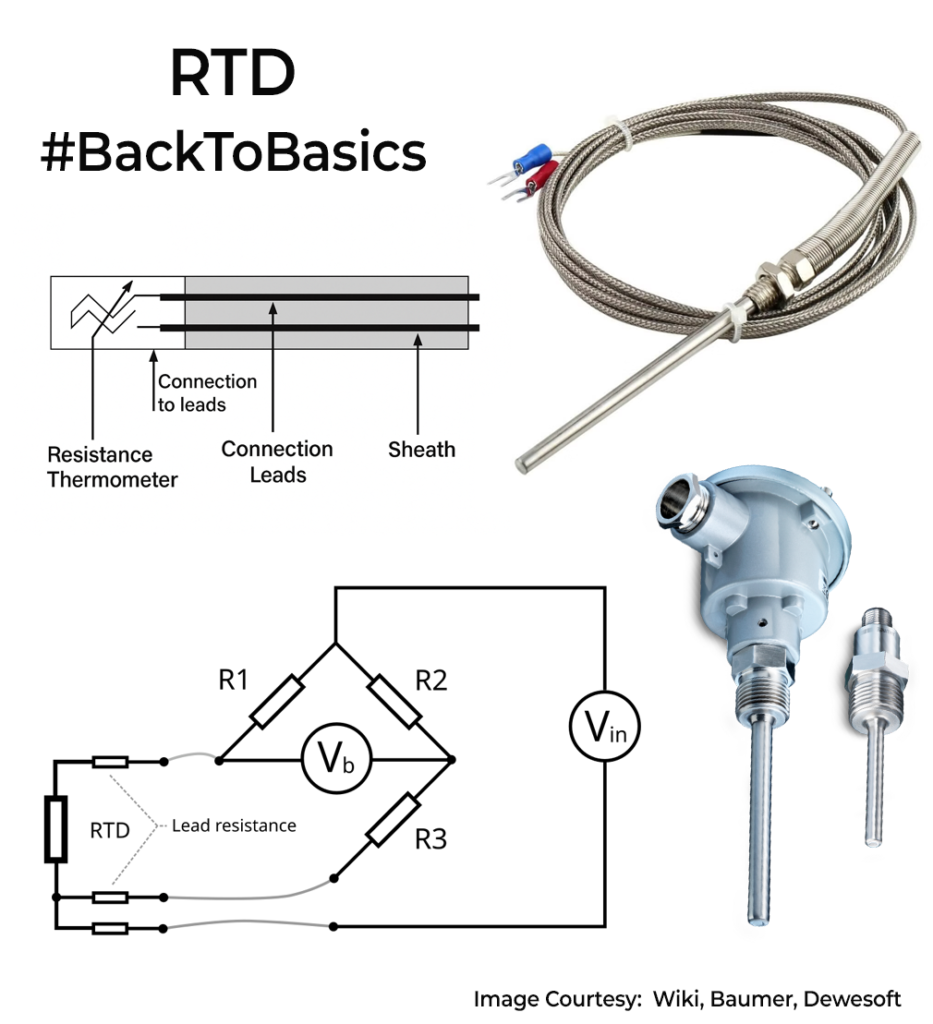
Sensing wires in RTDs are typically made from metals like platinum (Pt), Nickel, or Copper. Common ones are named Pt100 and Pt1000 because they indicate the resistance at a base temperature of 0 °C – Pt100 has 100Ω resistance, and Pt1000 has 1000Ω. So Pt1000 will have higher resolution. IEC 60751 is the international standard that specifies the temperature‑vs‑resistance relationship, accuracy tolerance classes (e.g. Class A, Class B) for industrial platinum RTDs. Based on construction type, Platinum RTDs can be wire-wound around a substrate, thin film pattern deposited on a substrate, or coiled wire type.
RTDs are split based on sensing wire configurations, as 2-wire, 3-wire, and 4-wire types. The 2-wire RTD is the simplest and cheapest, but it includes lead wire resistance in its measurement, causing accuracy limitations. The 3-wire RTD compensates for lead wire resistance by measuring the resistance in the third wire, significantly increasing accuracy for most industrial applications. The 4-wire RTD provides the highest accuracy by fully eliminating lead wire resistance errors, making it ideal for precision measurements.
RTDs particularly superior in precision applications ranging from -200 °C to 600 °C compared with thermocouples. Its output is linear, and Platinum elements change very little over time, minimizing recalibration frequency. Very good for long term use with minimal drift under 0.1 °C in industrial and medical devices.
Practical tip: choose wire-wound elements for stability, thin-film for quick response and compactness, or coiled-film if you need the best of both worlds, especially under vibration.
Try them out in your projects if you haven’t already. ????